

Digital footprints analyzed constantly
Assess user quality in the background
Determine the risk level even before traditional KYC procedures, by analyzing 300+ digital user footprints and identifying fraudsters at an early stage
What is Social Rating

How does it work?
C-Score uses a comprehensive approach to user analysis, combining multiple data sources to accurately determine the risk level. The system collects digital footprints, identifies anomalies, and forms a trust rating - even before traditional verification.
Key stages of the system’s operation
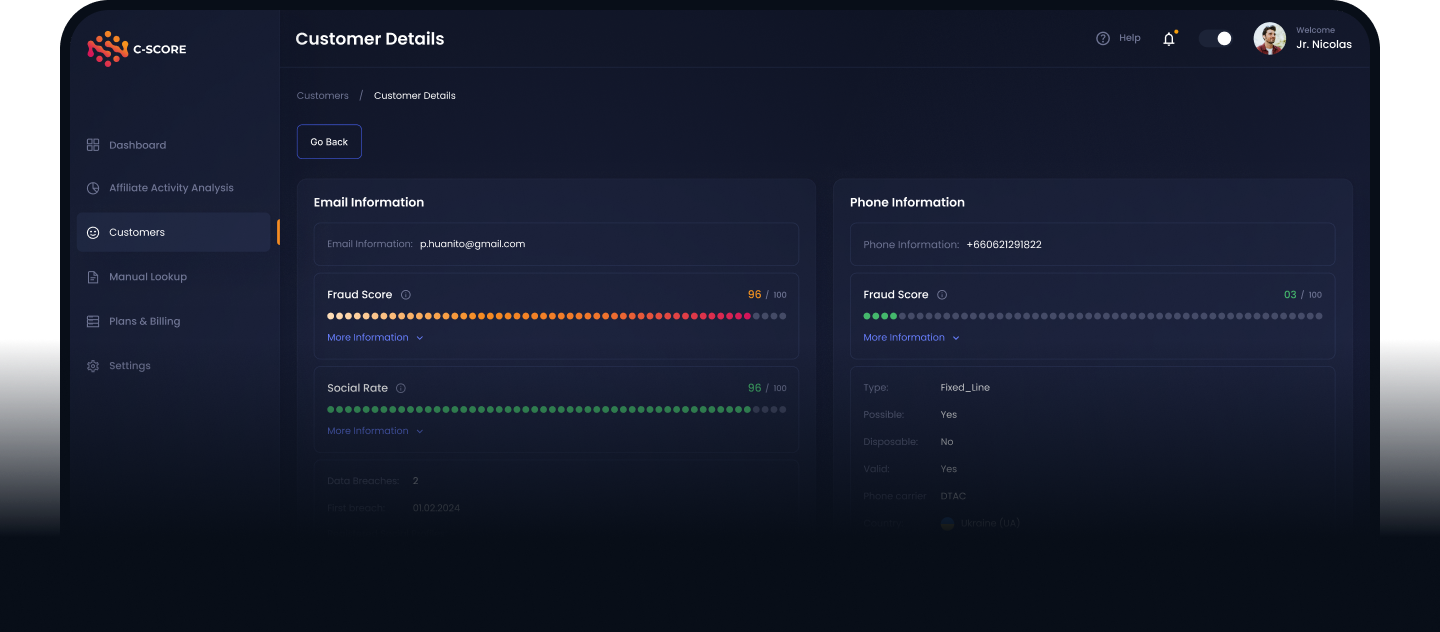
Email analysis
Temporary email signs, suspicious domains, data breaches
Phone Verification
Identification of temporary numbers, high-risk operators
IP Determination
Geolocation detection, VPN/proxy usage, and other address spoofing signs
Device Digital Fingerprinting
Language settings, IP time, screen resolution, installed plugins, hardware characteristic
The benefits that make your business safer
92%
Accuracy of algorithms
90%
Accuracy in identifying users
who will never be
profitable
8 out of 10
Cases of detecting traffic
source spoofing
Data analysis and anomaly detection
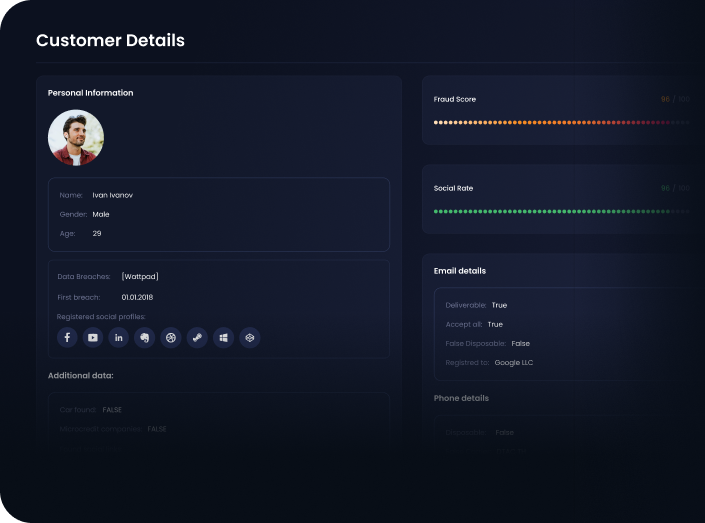
Risk Rating Formation
Try Social Rating and find out how secure your audience is
Fill out the feedback form and find out how your business can go beyond standard protection and achieve tangible growth
